One of the biggest risks to operational technology (OT) security is not a zero-day rootkit, but the people onsite day in and day out.
 Understanding and Mitigating Insider Threats in Operational Technology (OT) Systems
Understanding and Mitigating Insider Threats in Operational Technology (OT) Systems

Logan Carpenter | Dragos
One of the biggest risks to operational technology (OT) security is not a zero-day rootkit, but the people onsite day in and day out. The amount of access and control employees and contractors have in these environments could enable an insider threat to inflict severe collateral damage or potential loss of life.
What Is An Insider Threat?
An insider threat is anyone who has had or holds authorized access to information technology (IT) and OT resources, and who could intentionally or unintentionally compromise the security of an organization.
What Risk Do They Pose?
Insider threats are a growing problem. A Ponemon Institute survey shows that from 2018 to 2020 the number of insider threat incidents increased by 47%.1 Also, according to Ponemon, in the past two years this number has increased an additional 44%.2 However, there are other sources claiming that numbers have increased 72% in the past two years.3 Also, most companies that suffer from these incidents experience more than 30 attacks per year.1 The prominence of these attacks is growing year after year and is expected to continue increasing.
There are significant legal, safety, and financial implications that result from breaches of security. These security incidents could potentially cause:
- Loss of life
- Personal injury
- Denial of service
- Breach of privacy
- Loss of intellectual property
- Damage to company property
- Failure to meet regulatory compliance
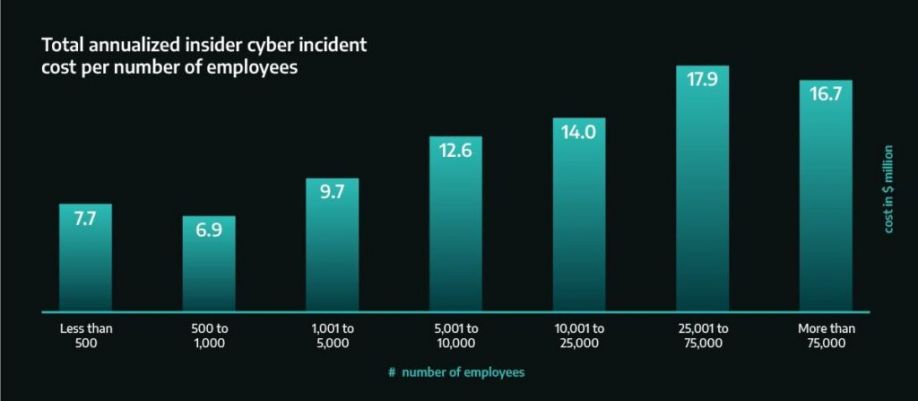
Figure 1: Total Annualized Insider Cyber Incident Cost Per Number of Employees4
As Figure 1 shows, these cyber events caused by insider threats all come with financial losses that could devastate an organization or even an entire industry. Research has shown that insider incidents on average take 85 days (about three months) to contain. Also, only 12% are contained in under 30 days.2 Furthermore, the smaller the organization, the more significant the fiscal impact is, as shown above.
Why Are Insider Threats So Difficult to Mitigate?
There are really two simple reasons why insider threats are difficult to mitigate:
- Humans are complex and unpredictable.
- Organizations must trust their employees.
Whether it is an accident, a motivated attack, or just simply gross negligence, an organization cannot predict what each of its employees will do. In OT environments, the risk tends to be greater because these individuals tend to be highly skilled technically and are required to have more access and control over these systems. The nature of OT environments requires them to have emergency override mechanisms in place to prevent disastrous situations such as equipment failure, system overload, or safety concerns. The fallout of an insider attack could affect the safety of others or even public health. When compared to other industries, critical infrastructure was placed second, only behind the technology industry, for most super malicious incidents.3 These are cases where the insider was highly skilled, and the techniques used were technically sophisticated.
Reasons Insider Threat Incidents Occur
Before you can mitigate insider threat incidents you must understand what causes them to occur. There are many reasons insider attacks occur; however, in general, all insider threats can fall under three categories: human error, a disgruntled employee, or externally motivated.
Human Error
This is when an insider simply fails to do their job properly. The employee could be undertrained, distracted, forgetful, exhausted, or negligent. No matter the cause, if their actions or lack of actions cause a breach of security they are considered an insider threat.
Human error is prevalent. Empirical studies have shown that 80-90% of accidents in industrial environments are due to human error.5 One research study’s data revealed that human error accounted for 56% of insider threat incidents they surveyed and cost organizations an average of $6.6 million per year.2
Disgruntled Employee
This is when a member has malicious intentions based on a vendetta they have with the organization or another member of the organization. The world witnessed this in the Maroochy attack where a disgruntled contractor of a wastewater company carried out a series of attacks on a city’s sewage system. The city council had recently rejected this attacker’s job application and the attacker got revenge by causing millions of gallons of raw sewage to spill into public areas.6 Another could be an employee who does not agree with certain organizational activities and wishes to release sensitive information to the public. These are both situations where the insiders are disgruntled with their organizations. Palo Alto Network’s incidence response branch, Unit-42, reported that 75% of the insider threat incidents they responded to were caused by a malicious ex-employee.7
Externally Motivated
This is when the insider is motivated to breach security by some factor outside the organization. An insider could be suffering from a life crisis, mental health issues, family issues, greed, and many others. The common thread is that the individual has malicious intentions. However, the motivation for the attack does not directly involve the organization. An example of this could be an employee engaging in intellectual property (IP) theft for financial gain.
Prevention & Detection
Although insider threats pose a risk to an organization’s OT and IT security, some measures can prevent or detect an insider attack.
More Visibility
Having more visibility in the OT and IT environments will enable an organization to detect unusual activity faster. A few types of mitigations for this include:
- Baseline and identify when accounts log in outside of their normal shift hours.
- Baseline and identify when employees badge in outside of normal physical areas.
- Identify when employees install new software, run new scripts, or access new network resources.
The visibility gained from the above mitigations will reduce the recovery time and fallout if an insider threat were to successfully breach security.
Assess Risks and Mitigate with Controls
An organization should know where its attack vectors are. Doing a crown jewel assessment will uncover all the areas that pose threats to the organization. Doing so enables the organization to put controls in place to prevent or detour malicious actors and have contingency plans in case of a breach.
Create a Culture of Security Competence
Establishing an organizational culture of security is vital when mitigating insider threats. Everyone from the CEO to contractors to the custodians needs to understand how to prevent security incidents. Other effective ways are posting cyber-related signs around the facility, regular cyber security training, security exercises and safety training. It helps to couple this with regularly scheduled conversations around safety. When everyone is aware of the security risks of their jobs, it reduces the chances of intentional and unintentional security incidents.
Be On the Lookout
Each member of the organization should be on the lookout for these psycho-social indicators amongst their coworkers.8
- Disgruntlement
- Not accepting feedback
- Anger management issues
- Disengagement or disregard for authority
- Stress
- Confrontational behaviors
- Lack of dependability
- Absenteeism
In short, employees should be encouraged to follow this advice: “when you see something, say something.”
Rotation and Separation of Duties
If an insider threat has too much control and little oversight, it enables them to carry out much more costly attacks. Separating responsibilities and access across multiple individuals will make it more difficult for a single insider to cause large-scale damage. This method, when allowable, prevents a single point of failure. However, there are cases where this may not be feasible, smaller organizations may need to have a system that monitors the insider’s interactions with the environment. For example, a system where the user’s interactions are logged and audited regularly.
In Conclusion
There is no bulletproof method of preventing insider threats. Humans are too unpredictable and impossible to control. However, the cost of doing nothing to mitigate these attacks could cripple an organization. Therefore, by implementing the guidelines explained in this blog an organization could prevent a catastrophic security incident.
Previously published on Dragos.com
References
- 2020 Cost of Insider Threats Global Threat – Ponemon
- 2022 Cost of Insider Threat Global Threat – Ponemon
- 2022 Insider Threat Risk Report – DTEX
- Total Annualized Cyber Incident Cost per Number of Employees – CISA
- Human error – OHSWiki Occupational Safety and Health (OSH) Wiki
- Hacker jailed for revenge sewage attacks – The Register
- 2022 Unit 42 Incident Response Report – Unit 42
- Identifying at-Risk Employees – PNNL
The content & opinions in this article are the author’s and do not necessarily represent the views of ManufacturingTomorrow
Comments (0)
This post does not have any comments. Be the first to leave a comment below.
Featured Product

